The Access Control Lists (ACL) Enhancements initiative introduces a file-based approach, with a user interface, to managing backend permissions in TYPO3. It builds upon previous efforts but redefines them with permission sets: deployable, versionable, and integrator-friendly configuration files. With the new ACL Enhancements (acl_enhancements) extension, permissions can be exported, imported, edited, and distributed across environments.
Key benefits include:
- Consistency through a single source of truth
- Deployable and version-controlled ACLs
- Editor-friendly workflows for creating and managing presets
- Extensibility via third-party extension presets and custom file writers
- Debugging and auditing tools that provide visibility into permission usage
Background and Motivation
We wanted to make a standalone extension to give the community critical improvements to TYPO3 workflow. We rebased previous ACL-related work, extracted functionality from patches, and then extended compatibility to TYPO3 v13 and began developing additional features.
The goal was to make permission sets usable in real life by the community.
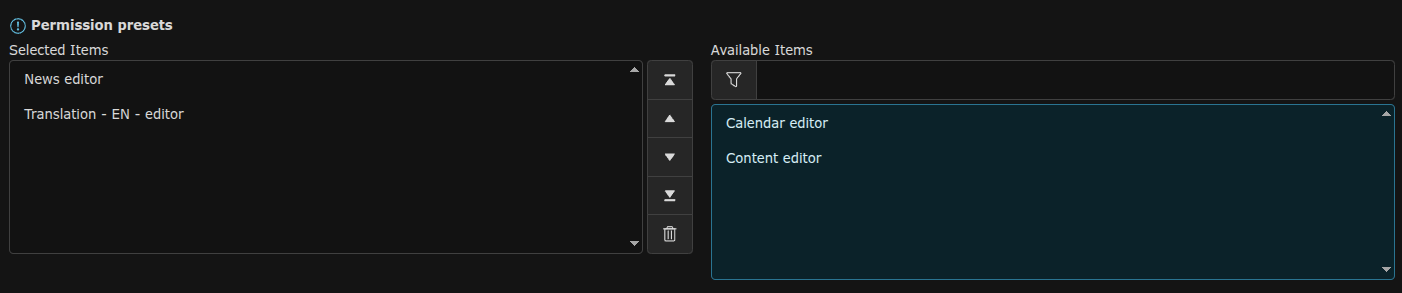
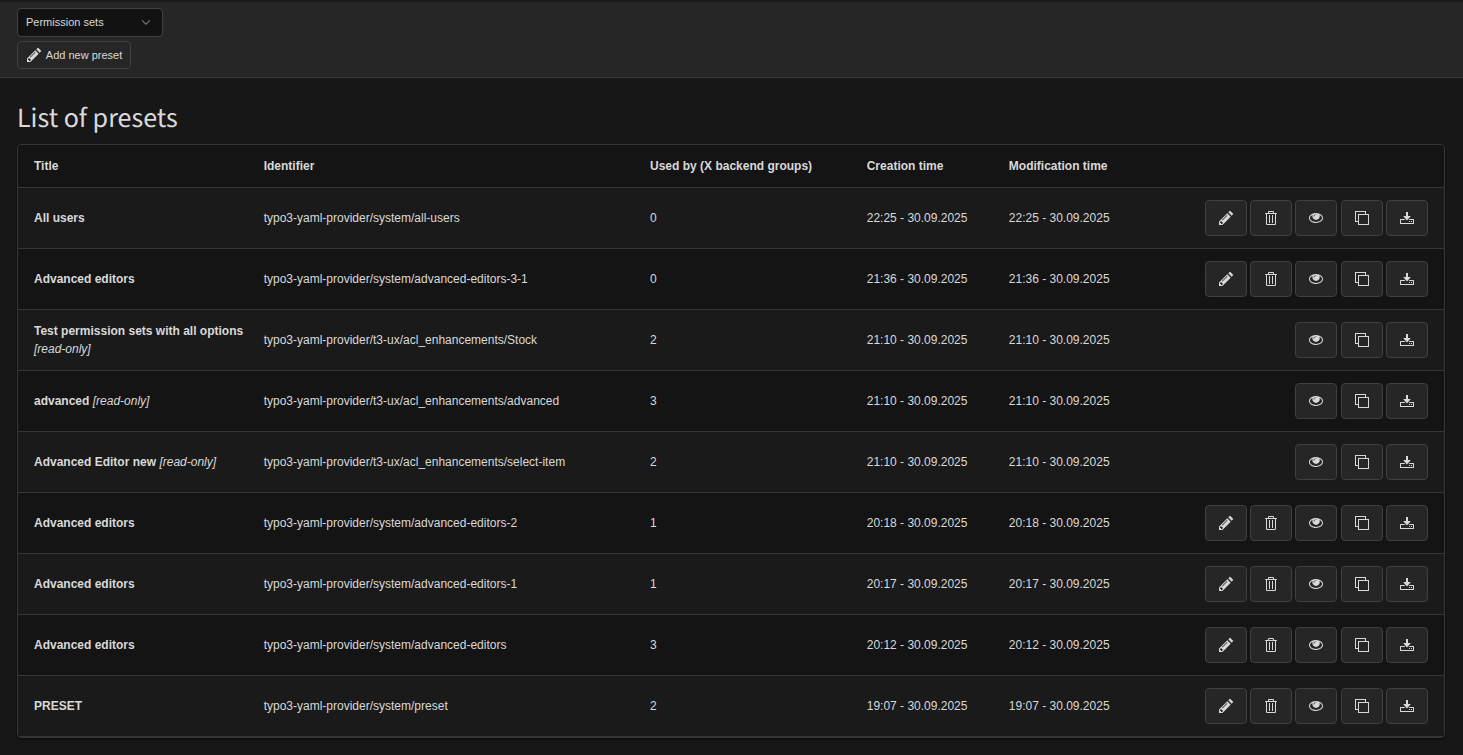
What is a Permission Set?
A permission set is a file that fully describes ACL rules for a backend group. It represents all selections from the group’s configuration, stored outside the database.
- Where it lives:
- Configuration/PermissionSets/ inside any extension
- config/permission-sets/ at the installation level (default export location)
- Why it matters:
- Enforces a single source of truth: if a field is managed by a permission set, it cannot also be modified in the database.
- Keeps backend groups lightweight - they only reference permission sets.
- Enables deployment and version control for ACLs, just like code.
Think of a permission set as infrastructure-as-code for TYPO3 ACLs.





![Screenshot showing a section titled Table permissions with tags [tables_select, tables_modify], and a message stating: This field is managed by selected permission sets: typo3-yaml-provider/system/all-users.](/fileadmin/t3o_common_storage/news/2025/10/acl/acl-image3.png)
![Screenshot showing the text: Used by following backend user groups: [usedIn] and a bullet point for Advanced editors [uid: 5] underneath.](/fileadmin/t3o_common_storage/news/2025/10/acl/acl-image1.png)