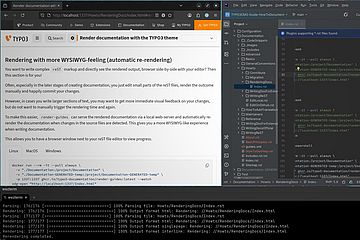
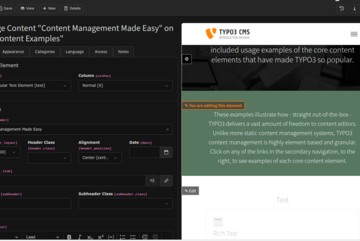
TYPO3 13.4.20 and 12.4.39 maintenance releases published
Categories:
Development,
TYPO3 CMS
The versions 13.4.20 and 12.4.39 of the TYPO3 Enterprise Content Management System have just been released.
Read more