Solutions Are Coming—Testers Needed
We are planning a regression bugfix release (11.3.3, 10.4.20, 9.5.30) as soon as possible, once enough people have reviewed our proposed changes.
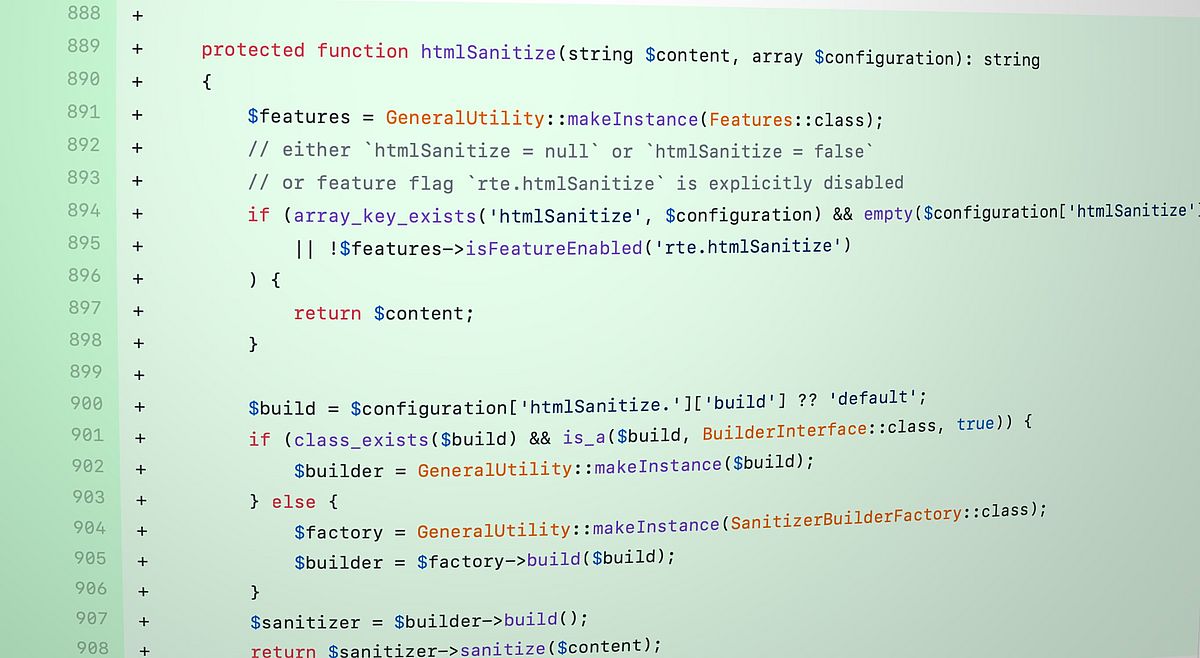
We will also ship a new ViewHelper for Fluid: <f:sanitize.html>. It can be used if people just want to make sure that it is safe to re-render user-submitted content.
We are aware that only a small group of people can test the security bug fixes before the release, especially in real-life projects with lots of custom setup code. We are actively looking for developers and companies, willing to help us test security changes before they are released. Please reach out to security(at)typo3.org if you would like to help us test changes before they are released.
We need contributions to write documentation on best practices, for example how to choose the right ViewHelper for a given situation, and how to structure and separate data in templates in a better way.