Content Preview: The Journey of a Side-By-Side Budget Idea
Categories:
Budget idea,
Development,
Community
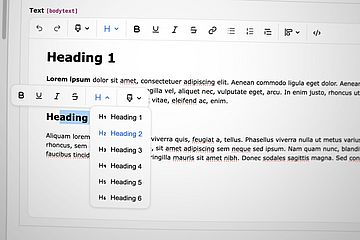
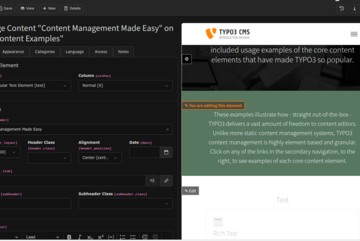
In this report, Łukasz Uznański shares the story behind his community budget idea and presents the first results of the new Content Preview extension.
Read more