- Component Type: TYPO3 CMS
- Subcomponent: File Upload Handling (ext:core, ext:filelist, ext:backend, ext:frontend)
- Release Date: December 17, 2019
- Vulnerability Type: Cross-Site Scripting
- Affected Versions: All
- Severity: medium
- Suggested CVSS v3.1: AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N/E:F/RL:T/RC:C
Problem Description
TYPO3 allows to upload files either in the backend user interface as well as in custom developed extensions. To reduce the possibility to upload potential malicious code TYPO3 uses the fileDenyPattern to deny e.g. user submitted PHP scripts from being persisted. Besides that it is possible for any editor to upload file assets using the file module (fileadmin) or changing their avatar image shown in the TYPO3 backend.
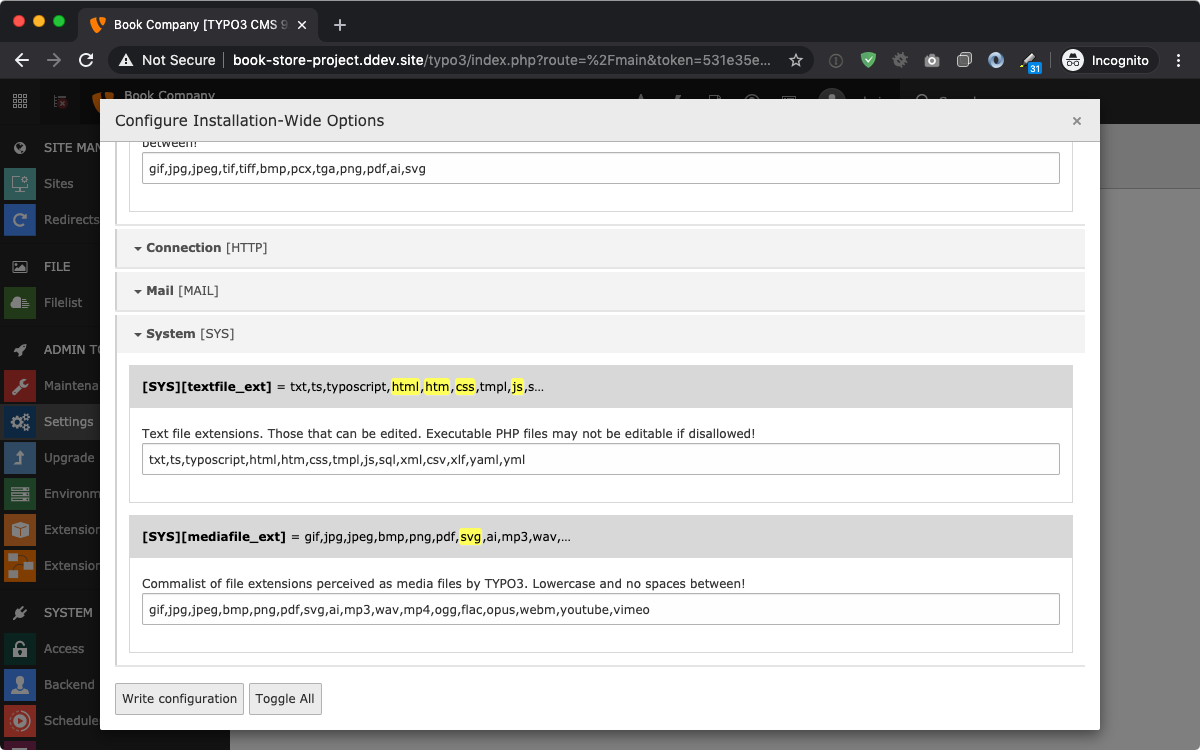
Per default TYPO3 allows to upload and store HTML and SVG files as well using the mentioned functionalities. Custom extension implementations probably would also accept those files when only the fileDenyPattern is evaluated.
Since HTML and SVG files - which might contain executable JavaScript code per W3C standard - could be directly displayed in web clients, the whole web application is exposed to be vulnerable concerning Cross-Site Scripting. Currently the following scenarios are known - given an authenticated regular editor is able to upload files using the TYPO3 backend:
- directly target a potential victim to a known public resource in a URL, e.g. /fileadmin/malicious.svg or /fileadmin/malicious.html
- using the TypoScript content object “SVG” (implemented in class ScalableVectorGraphicsContentObject) having renderMode set to inline for SVG files (available since TYPO3 v9.0)
- custom implementations that directly output and render markup of HTML and SVG files
SVG files that are embedded using an <img src=”malicious.svg”> tag are not vulnerable since potential scripts are not executed in these scenarios (see https://www.w3.org/wiki/SVG_Security). The icon API of TYPO3 is not scope of this announcement since SVG icons need to be registered using an individual implementation, which is not considered as user submitted content.
Solution
The real solution to avoid user submitted content and Cross Site Scripting in HTML and SVG files is to disable the possibility to upload those files in general. The TYPO3 install tool provides according settings in TYPO3_CONF_VARS/SYS which shall not contain HTML and SVG file extensions anymore.